
Mar 7, 2025 | Cyber Crime, Cyber Security, Data Back Up, News, Security, Trends
With the ever-growing threat of cyber attacks and data breaches, all businesses, big or small, need to stay ahead of the game when it comes to cyber security. At BITS, we specialise in helping businesses secure their IT estate, and we want to help you understand how...

Jan 16, 2025 | Cyber Security, News, Trends
In 2025, Windows 10 will officially reach its end-of-life status, marking the conclusion of Microsoft’s mainstream support for the operating system that has been a staple for businesses and individuals alike since its launch in 2015. But what does this mean for your...
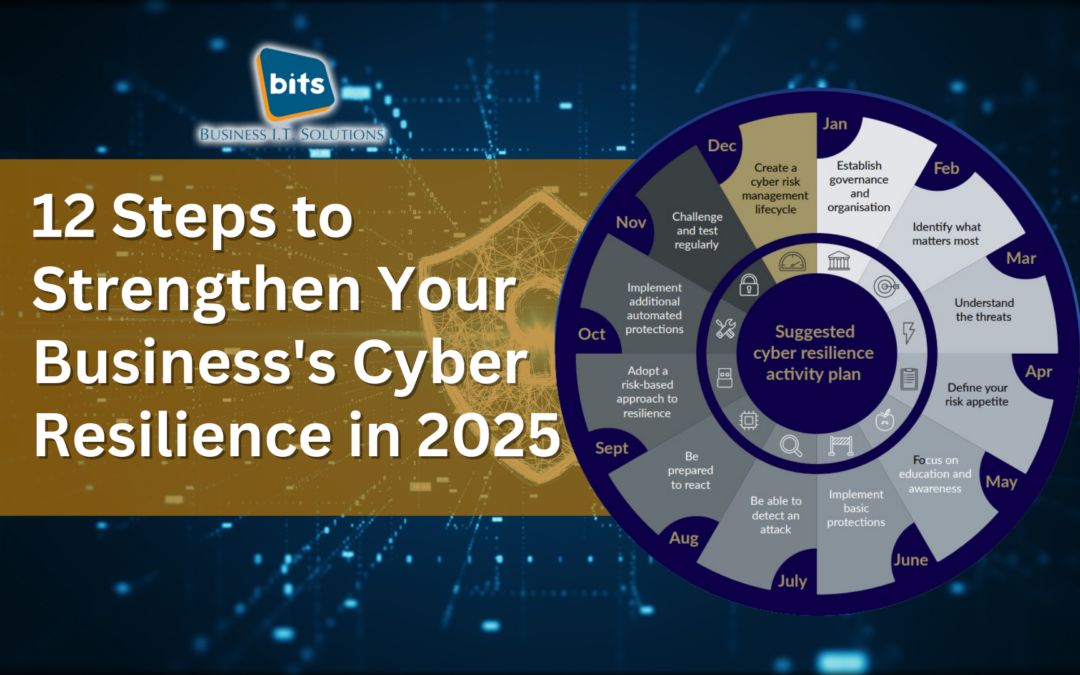
Jan 16, 2025 | Cyber Security, News, Trends
In today’s interconnected world, cyber risk is a prevalent and critical concern for businesses of all sizes. As technology advances, so do the threats posed by cybercriminals, making robust cybersecurity essential for safeguarding your operations, reputation, and...

Nov 8, 2024 | Cyber Security, News, Trends
January 2025 is just around the corner! The Digital Operational Resilience Act (DORA) will soon become law across the EU, meaning financial institutions in Ireland must meet stringent new requirements for cyber resilience and operational continuity. Is your...

Oct 10, 2024 | News, Cyber Security, Trends
In today’s digital age, cyber security has become a critical concern for businesses worldwide. As companies increasingly rely on digital infrastructure, the risks associated with cyber threats have grown exponentially. This is particularly true in the context of...

Oct 8, 2024 | Trends, Cyber Security, News
Enterprise Ireland (EI) and the National Cyber Security Centre (NCSC) have launched the new Cyber Security Review Grant, designed to assist Irish SMEs in reviewing and strengthening their cyber security. This grant is an incredible opportunity for businesses to take...







